First published: 19th of August 2014 for Orbit Media Studios
Passwords are a pain. They are required for too many things; your phone, your computer, your apps, your accounts. They get in the way of getting something done.
It would be wonderful if this post was an introduction to something better. Alas, for the time being, we’re stuck with passwords. So, how can we best use them? How can we secure ourselves and others? What, exactly is a “strong” password?
Let’s start by considering the opposite, what makes a password weak?
These examples are considered weak because they are based on simple patterns that are easy to guess and trivial for an automated process to test at high speeds. More to the point, common words and patterns expose the two main problems with many passwords; different people with the same cultural influences and one person reusing a password multiple times.
Let’s put on the black hat for a moment and consider the problem. We want to gain access to someone’s account. Let’s consider the account in question and begin to create a list of possible passwords.
For each word…
With this dictionary of words to try and a process to try them with we can now make an automated attempt at accessing the account.
But wait, you might be thinking, how large of a list does this really have to be? One study by security consultant Mark Burnett determined that in a pool of over 6,000,000 unique accounts, a list with 1,000 of the most frequent passwords will match 91% of the accounts. Increase the list to 10,000 and now we have access to 99.8% accounts.
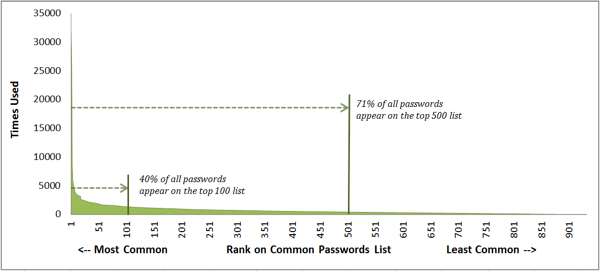
And once we’ve gained access to an account the chances that the user has used the same password elsewhere will increase. A 2014 research study estimated that, “43- 51% of users reuse the same password across multiple sites.” Moreover, knowing a user’s password also increases the chance of guessing a variation of the known password in use elsewhere.
Guidelines for what constitutes a strong password will vary, based on a number of conditions, such as:
With these conditions in mind, the main goal is to lower the ability of an aided attacker from guessing what the password is, therefore;
And to keep track of your newly created, randomly long passwords? Use a secure password manager which will store all your passwords encrypted with a master password key.
But take note, while some password managers store passwords locally on your device, others store the data on a server elsewhere on the Internet. Which storage method is right for you will depend on your aversion to risk.